Key-leaking side channels are a fact of life. Now they can be done by video-recording power LEDs.
Enlarge / Left: a smart card reader processing the encryption key of an inserted smart card. Right: a surveillance camera video records the reader’s power LED from 60 feet away.
Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video record power LEDs that show when the card reader or smartphone is turned on.
The attacks enable a new way to exploit two previously disclosed side channels, a class of attack that measures physical effects that leak from a device as it performs a cryptographic operation. By carefully monitoring characteristics such as power consumption, sound, electromagnetic emissions, or the amount of time it takes for an operation to occur, attackers can assemble enough information to recover secret keys that underpin the security and confidentiality of a cryptographic algorithm.
Side-channel exploitation made simple
As Wired reported in 2008, one of the oldest known side channels was in a top-secret encrypted teletype terminal that the US Army and Navy used during World War II to transmit communications that couldn’t be read by German and Japanese spies. To the surprise of the Bell Labs engineers who designed the terminal, it caused readings from a nearby oscilloscope each time an encrypted letter was entered. While the encryption algorithm in the device was sound, the electromagnetic emissions emanating from the device were enough to provide a side channel that leaked the secret key.
Side channels have been a fact of life ever since, with new ones being found regularly. The recently discovered side channels tracked as Minerva and Hertzbleed came to light in 2019 and 2022, respectively. Minerva was able to recover the 256-bit secret key of a US-government-approved smart card by measuring timing patterns in a cryptographic process known as scalar multiplication. Hertzbleed allowed an attacker to recover the private key used by the post-quantum SIKE cryptographic algorithm by measuring the power consumption of the Intel or AMD CPU performing certain operations. Given the use of time measurement in one and power measurement in the other, Minerva is known as a timing side channel, and Hertzbleed can be considered a power side channel.
On Tuesday, academic researchers unveiled new research demonstrating attacks that provide a novel way to exploit these types of side channels. The first attack uses an Internet-connected surveillance camera to take a high-speed video of the power LED on a smart card reader—or of an attached peripheral device—during cryptographic operations. This technique allowed the researchers to pull a 256-bit ECDSA key off the same government-approved smart card used in Minerva. The other allowed the researchers to recover the private SIKE key of a Samsung Galaxy S8 phone by training the camera of an iPhone 13 on the power LED of a USB speaker connected to the handset, in a similar way to how Hertzbleed pulled SIKE keys off Intel and AMD CPUs.
Power LEDs are designed to indicate when a device is turned on. They typically cast a blue or violet light that varies in brightness and color depending on the power consumption of the device they are connected to.
There are limitations to both attacks that make them unfeasible in many (but not all) real-world scenarios (more on that later). Despite this, the published research is groundbreaking because it provides an entirely new way to facilitate side-channel attacks. Not only that, but the new method removes the biggest barrier holding back previously existing methods from exploiting side channels: the need to have instruments such as an oscilloscope, electric probes, or other objects touching or being in proximity to the device being attacked.
In Minerva’s case, the device hosting the smart card reader had to be compromised for researchers to collect precise-enough measurements. Hertzbleed, by contrast, didn’t rely on a compromised device but instead took 18 days of constant interaction with the vulnerable device to recover the private SIKE key. To attack many other side channels, such as the one in the World War II encrypted teletype terminal, attackers must have specialized and often expensive instruments attached or near the targeted device.
The video-based attacks presented on Tuesday reduce or completely eliminate such requirements. All that’s required to steal the private key stored on the smart card is an Internet-connected surveillance camera that can be as far as 62 feet away from the targeted reader. The side-channel attack on the Samsung Galaxy handset can be performed by an iPhone 13 camera that’s already present in the same room.
“One of the most significant things of this paper is the fact that you don’t need to connect the probe, connect a scope, or use a software-defined radio,” Ben Nassi, the lead researcher of the attack, said in an interview. “It’s not intrusive, and you can use common or popular devices such as a smartphone in order to apply the attack. For the case of the Internet-connected video camera, you don’t even need to approach the physical scene in order to apply the attack, which is something you cannot do with a software-defined radio or with connecting probes or things like this.”
The technique has another benefit over more traditional side-channel attacks: precision and accuracy. Attacks such as Minerva and Hertzbleed leak information through networks, which introduces latency and adds noise that must be compensated for by collecting data from large numbers of operations. This limitation is what causes the Minerva attack to require a targeted device to be compromised and the Hertzbleed attack to take 18 days.
Rocking the rolling shutter
To many people’s surprise, a standard video camera recording a power LED provides a means of data collection that is much more efficient for measuring information leaking through a side channel. When a CPU performs different cryptographic operations, a targeted device consumes varying amounts of power. The variations cause changes in brightness and sometimes colors of the power LEDs of the device or of peripherals connected to the device.
To capture the LED variations in sufficient detail, the researchers activate the rolling shutter available in newer cameras. Rolling shutter is a form of image capture akin in someways to time-lapse photography. It rapidly records a frame line by line in a vertical, horizontal, or rotational fashion. Traditionally, a camera could only take pictures or videos at the speed of its frame rate, which maxed out at 60 to 120 frames per second.
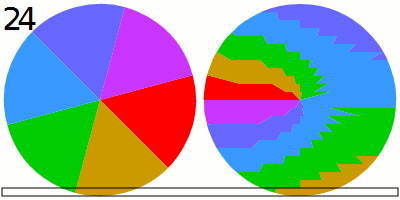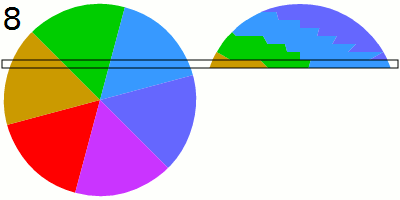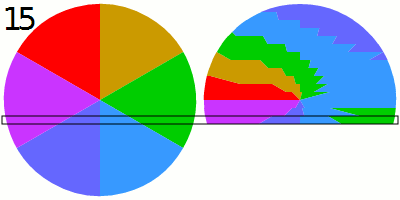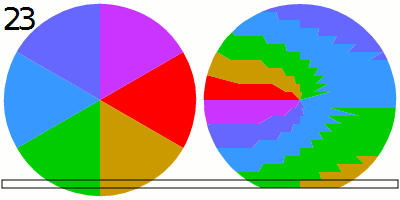
Activating a rolling shutter can upsample the sampling rate to collect roughly 60,000 measurements per second. By completely filling a frame with the power LED that’s presently on or connected to a device while it performs cryptographic operations, the researchers exploited the rolling shutter, making it possible for an attacker to collect enough detail to deduce the secret key stored on a smart card, phone, or other device.
“This is possible because the intensity/brightness of the device’s power LED correlates with its power consumption, due to the fact that in many devices, the power LED is connected directly to the power line of the electrical circuit which lacks effective means (e.g., filters, voltage stabilizers) of decoupling the correlation,” the researchers wrote in Tuesday’s paper.
They continued:
We empirically analyze the sensitivity of video cameras and show that they can be used to conduct cryptanalysis because: (1) the limited eight-bit resolution (a discrete space of 256 values) of a single RGB channel of video footage of a device’s power LED is sufficient for detecting differences in the device’s power consumption which are caused by the cryptographic computations, and (2) the video camera’s rolling shutter can be exploited to upsample the sampling rate of the intensity/brightness of the power LED in the video footage to the level needed to perform cryptanalysis, i.e., increasing the number of measurements (sampling rate) of the intensity/brightness of the power LED in video footage by three orders of magnitude from the FPS rate (which provides 60–120 measurements per second) to the rolling shutter rate (which provides 60K measurements per second in the iPhone 13 Pro Max), by zooming the video camera on the power LED of the target device so the view of the LED fills the entire frame of the video footage. By doing so, attackers can use a video camera as a remote invasive alternative to the professional dedicated sensors which are usually used to conduct cryptanalysis (e.g., a scope, software-defined radio).
Videos here and here and displayed below show the video-capture process of a smart card reader and Samsung Galaxy phone, respectively, as they perform cryptographic operations. To the naked eye, the captured video looks unremarkable.
To the naked eye, the captured video looks unremarkable.
But by analyzing the video frames for different RGB values in the green channel, an attacker can identify the start and finish of a cryptographic operation.


Some restrictions apply
Here are the threat models assumed in the research:
A target device is creating a digital signature or performing a similar cryptographic operation on a device. The device has either a standard on/off type 1 or indicative power type 2 power LED, which maintains a constant color or a changing color in response to triggered cryptographic operations. If the device doesn’t have a type 1 or type 2 power LED, it must be connected to a peripheral device that does. The brightness or color of these power LEDs must correlate to the power consumption of the device.
The attacker is a malicious entity in a position to constantly video-record the power LED of either the device or a peripheral device such as USB speakers while the cryptographic operation is taking place.
In the smart card reader’s case, the attacker acquires video by first hacking a surveillance camera that’s up to 60 feet away from—and has line of sight to—the reader’s power LED. The camera compromise must allow the attacker to control the zoom and rotation of the camera. Given numerous instances of Internet-connected video cameras being actively hacked by researchers, real-world botnet operators, and other threat actors, the assumption in the current attack isn’t an especially tall order.
When the camera is 60 feet away, the room lights must be turned off, but they can be turned on if the surveillance camera is at a distance of about 6 feet. (An attacker can also use an iPhone to record the smart card reader power LED.) The video must be captured for 65 minutes, during which the reader must constantly perform the operation.
For the Samsung Galaxy, the attacker must be able to record the power LED of USB-connected speakers from a fairly close range while the handset performs a SIKE signing operation.
The attack assumes there is an existing side channel that leaks power consumption, timing, or other physical manifestations of the device as it performs a cryptographic operation. The smart cards inserted into the readers used a code library that had yet to be patched against the Minerva attack. A library used by the Samsung Galaxy remained vulnerable against Hertzbleed. It’s likely that at least some side channels discovered in the future would also allow the attack to work.
The threat model significantly limits the scenarios under which the current attack works, so attacks aren’t likely to work against government-approved readers used on military bases or other high-security settings (the researchers didn’t test any of these).
That’s because the card readers themselves are likely hardened, and even if they’re not, smart cards issued to personnel in these settings are rotated every couple of years to ensure they contain the latest security updates. Even if both a reader and smart card are vulnerable, the reader must process the card for a full 65 minutes, something that’s impossible during a standard card swipe at a security checkpoint.
But not all settings are as carefully restricted. All six of the smart card readers found to facilitate the attack are available on Amazon and are compatible with common access cards (known as CACs) used by the US military. Four of the readers are advertised with the words “DOD,” “military,” or both. It isn’t unusual for military or government personnel to use such card readers when logging in to non-classified networks from remote locations.
“In general, as long as the particular manufacturer and model are supported by your OS, the only other prerequisites to access DoD resources are (1) that you have the current root and intermediate DoD CAs installed for your OS to trust both your smart card certificate(s) and the certs of sites/services you’re connecting to and (2) that the resource in question is directly accessible from the public Internet (vs. connecting an internal VPN first),” Matt said in an interview. That account was similar to one given by a former Airforce contractor who said, “I never had specific CAC readers dictated to me. If they worked, we were fine.”
Restrictions in corporations, state or local governments, and other organizations are likely more lenient still.
Another limitation with the attack on the Samsung Galaxy is that the SIKE algorithm was taken out of the running as a post-quantum encryption contender following the discovery of an attack that uses complex mathematics and a single traditional PC to recover the secret key protecting encrypted transactions
In an emailed statement, Samsung officials wrote: “We can confirm that the hypothetical attack developed by researchers on the Galaxy S8 was reported to us in 2022, reviewed, and deemed low risk as the particular algorithm is not used on our devices. Consumer privacy is of the utmost importance, and we will keep our security protocols to the highest standard for all devices.”
Interesting, important, impressive
Despite the attack’s shortcomings, the results of the research are “definitely interesting and important,” particularly in the wake of the discovery of Hertzbleed and a similar attack known as Platypus, said Daniel Gruss, a researcher at Graz University of Technology who has helped discover several side channels, including ones here and here in Intel CPUs. In an email, he wrote:
There is a line of research that becomes increasingly relevant around attacks like Platypus, Hertzbleed, and attacks like this one. The basic issue is that power side-channel attacks are incredibly powerful in what information they can leak. For the past decades, this required physical equipment, making those attacks unrealistic in many real-world settings. Now, with remote software-based attacks or the video-recording-based/air-gapped attack presented in this paper, this really changes a lot.
Dan Boneh, a computer scientist and cryptographer at Stanford University, said in an interview that even taking the limitations into account, “it is still impressive that the attack works at all.”
Gruss also noted the common observation made by many researchers that attacks only get better over time with the discovery of new techniques and vulnerabilities.
Another factor potentially offsetting some of the limitations is the rapid pace of advances being made in cameras, which in a few years may increase the range or shorten the time required for the attack. The researchers wrote:
We also raise concern regarding the real potential of video-based cryptanalysis in our days, given existing improvements in video cameras’ specifications. In our research, we focused on commonly used and popular video cameras to demonstrate video-based cryptanalysis (i.e., 8-bit space for a single RGB channel, Full-HD resolution, and maximum supported shutter speed). However, new versions of smartphones already support video footage of 10-bit resolution (e.g., iPhone 14 Pro MAX and Samsung Galaxy S23 Ultra). Moreover, professional video cameras with a resolution of 12-14 bits already exist, 2 Such video cameras may provide much greater sensitivity, which may allow attackers to perform attacks with the ability to detect very subtle changes in the device’s power consumption via the intensity of the power LED. In addition, many Internet-
connected security cameras with greater optical-zoom capabilities than the video camera used in our research (25X) already exist (30X, 36X) and are likely already widely deployed. Such security cameras may allow attackers to perform video-based cryptanalysis against target devices from a greater distance than that demonstrated in this paper. Finally, new professional video cameras for photographers currently support a shutter speed of 1/180,000 (e.g, Fujifilm X-H2.3) The use of such video cameras may allow attackers to obtain measurements at a higher sampling rate which may expose other devices to the risk of video-based cryptanalysis.
The research is the result of a collaboration between The Urban Tech Hub at Cornell Tech and The Cyber Security Research Center at the Ben-Gurion University of the Negev. Besides Nassi, team members included Etay Iluz, Or Cohen, Ofek Vayner, Dudi Nassi, Boris Zadov, and Yuval Elovici.
The researchers recommend several countermeasures that manufacturers can take to harden devices against video-based cryptanalysis. Chief among them is avoiding the use of indicative power LEDs by integrating a capacitor that functions as a “low pass filter.” Another option is to integrate an operational amplifier between the power line and the power LED.
It’s not clear if or when manufacturers of affected devices might add such countermeasures. For now, people who are unsure about the vulnerability of their devices should consider placing opaque tape on power LEDs or using other means to block them from view.
Source: ARS TECHNICA


